Firewall Configuration in Cisco Packet Tracer
In this class we are going to configure the Firewall because firewall ensure the security for the internal organization.
We are going to use Cisco Packet Tracer version 8.0 for this class because in the previous 6.0.1 version the Firewall device was not available.
Download
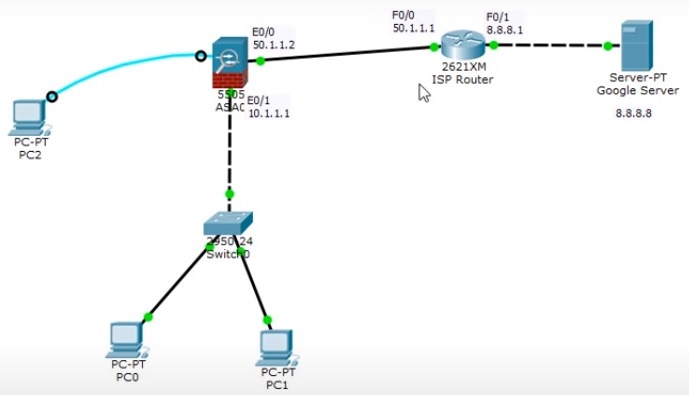
We have created a topology having a Firewall that is connected to a Router; Router is further connected to the DNS server.
Firewall has both internal part and external part; local internal setup is connected to the Firewall E0/1 port and the external part is connected to E0/0 port to the Router for receiving external traffic.
First let us assign the static IP Address to the DNS server manually;
Open the interface and type in the static IP Address field 8.8.8.8 and provide subnet 255.0.0.0 and also provide the gateway as 8.8.8.1 because DNS sever is connected with the Router port Fa0/1; where we are going to assign IP Address of that port as 8.8.8.1.
Now let us configure and set the IP Address of the Router;
Continue with configuration dialog? [yes/no]:no
Router>enable
Router#configure terminal
Router(config)#interface fastEthernet 0/0
Router(config-if)#ip address 50.1.1.1 255.0.0.0
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#interface fastEthernet 0/1
Router(config-if)#ip address 8.8.8.1 255.0.0.0
Router(config-if)#no shutdown
Router(config-if)#exit
Now set the OSPF on Router;
Router(config)#router ospf 1
Router (config-router)#network 50.0.0.0 0.255.255.255 area 0
Router (config-router)#network 8.0.0.0 0.255.255.255 area 0
Router (config-router)#exit
Router(config)#exit
Router#write
Building configuration...
[OK]
Router#exit
Router>
Therefore we have completed assigning the IP Addresses to the Router ports Fa0/0 and Fa0/1.
Let us start configuring the Firewall and assign IP Addresses;
ciscoasa>enable
Password is set blank by default (press enter)
Password:
ciscoasa#configure terminal
Set IP Address to VLAN-1
ciscoasa(config)#interface vlan 1
ciscoasa(config-if)#ip address 10.1.1.1 255.0.0.0
ciscoasa(config-if)#no shutdown
ciscoasa(config-if)#nameif inside
ciscoasa(config-if)#security-level 100
ciscoasa(config-if)#exit
ciscoasa(config)#interface E0/1
ciscoasa(config-if)#switchport mode access
ciscoasa(config-if)#switchport access vlan 1
ciscoasa(config-if)#exit
ciscoasa(config)#interface vlan 2
ciscoasa(config-if)#ip address 50.1.1.2 255.0.0.0
ciscoasa(config-if)#no shutdown
ciscoasa(config-if)#nameif outside
ciscoasa(config-if)#security-level 0
ciscoasa(config-if)#exit
ciscoasa(config)#interface E0/0
ciscoasa(config-if)#switchport mode access
ciscoasa(config-if)#switchport access vlan 2
ciscoasa(config-if)#exit
Now allow DHCP and DNS services in the Firewall; so that the internal computers can obtain the IP Addresses along with the subnet and DNS automatically from the Firewall.
ciscoasa(config)#dhcpd address 10.1.1.10-10.1.1.30 inside
ciscoasa(config)#dhcpd dns 8.8.8.8 interface inside
Now configure the default route of the Firewall; therefore through the Router Port Fa0/0 of IP Address 50.1.1.1; any traffic of any subnet can pass.
ciscoasa(config)#route outside 0.0.0.0 0.0.0.0 50.1.1.1
Create Object Network and enable NAT on Firewall;
ciscoasa(config)#object network LAN
ciscoasa(config-network-object)#subnet 10.0.0.0 255.0.0.0
ciscoasa(config-network-object)#nat (inside, outside) dynamic interface
ciscoasa(config-network-object)#exit
Now create the access list and group list;
ciscoasa(config)#access-list oti extended permit tcp any any
ciscoasa(config)#access-list oti extended permit icmp any any
ciscoasa(config)#access-group oti in interface outside
ciscoasa(config)#exit
ciscoasa#write
Building configuration...
[OK]
ciscoasa#exit
ciscoasa>
So we have completed configuring the topology; if we check now by sending packet from the local computers to the DNS server or Router then the packet will pass through the Firewall.
We will also check by PING command from any local computer to access the DNS server.
Type in the command prompt (ping 8.8.8.8);
We will get successful reply in status.
How to Configure Firewall in Packet Tracer How to Configure Firewall in Cisco Packet Tracer Firewall Settings in Cisco Packet Tracer Firewall in Cisco Packet Tracer Firewall Configuration on Cisco Packet Tracer Firewall Configuration in Packet Tracer Firewall Configuration in Cisco Packet Tracer Firewall Cisco Packet Tracer Configuring Firewall Using Cisco Packet Tracer Configure Firewall in Cisco Packet Tracer ASA Firewall Configuration in Cisco Packet Tracer How to Configure Firewall in Packet Tracer How to Configure Firewall in Cisco Packet Tracer Firewall Settings in Cisco Packet Tracer Firewall in Cisco Packet Tracer Firewall Configuration on Cisco Packet Tracer Firewall Configuration in Packet Tracer Firewall Configuration in Cisco Packet Tracer Firewall Cisco Packet Tracer Configuring Firewall Using Cisco Packet Tracer Configure Firewall in Cisco Packet Tracer ASA Firewall Configuration in Cisco Packet Tracer How to Configure Firewall in Packet Tracer How to Configure Firewall in Cisco Packet Tracer Firewall Settings in Cisco Packet Tracer Firewall in Cisco Packet Tracer Firewall Configuration on Cisco Packet Tracer Firewall Configuration in Packet Tracer Firewall Configuration in Cisco Packet Tracer Firewall Cisco Packet Tracer Configuring Firewall Using Cisco Packet Tracer Configure Firewall in Cisco Packet Tracer ASA Firewall Configuration in Cisco Packet Tracer